1. Create an ipset that uses hash:net so we can block huge netblocks with CIDR notation.
ipset create blacklist hash:net
2. Then add the ip blocks you want to block to the blacklist ipset like below. More on this in step 4 but I believe you've got to have at least one net block in there to add the iptables rule.
ipset add blacklist 1.0.1.0/24
You can get country IP blocks here: http://www.ipdeny.com/ipblocks/data/aggregated/ http://www.ipdeny.com/ipblocks/
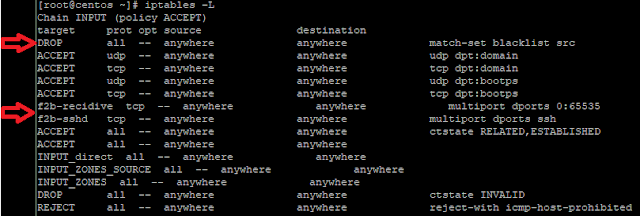
3. Then add a rule in iptables to DROP the blacklist in the position of line 1. I put it first in line so it gets executed before all other rules.
iptables -I INPUT 1 -m set --match-set blacklist src -j DROP
4. Fine tune/create your blacklist ipset and save it as a local file. This script will automatically add countries IP blocks to the "blacklist" ipset in memory. You still need to "ipset save blacklist > /etc/sysconfig/ipset.blacklist" after you get your ipset the way you want so you can load it at startup. I would recommend loading it from a local file instead of running the population script at boot time in case the ipdeny.com website is not available.
cd /root
nano RunIPSet
------------------Copy---------Credit for script is coming as soon as I find it again online-------------
#!/bin/bash
for IP in $(wget -O - http://www.ipdeny.com/ipblocks/data/aggregated/{cn-aggregated,ru-aggregated,kr-aggregated,pk-aggregated,tw-aggregated,sg-aggregated,hn-aggregated,hk-aggregated,ir-aggregated,ua-aggregated,vn-aggregated,it-aggregated,de-aggregated,my-aggregated,nl-aggregated,ng-aggregated,cf-aggregated,gt-aggregated,id-aggregated,ie-aggregated,il-aggregated,iq-aggregated,td-aggregated,za-aggregated,br-aggregated,ca-aggregated,dk-aggregated,fr-aggregated,in-aggregated,jp-aggregated,mx-aggregated,ph-aggregated}.zone)
do
sudo ipset add blacklist $IP
done
-------------------Save-------------------------------
This will take a long time to finish. It will look like it's not doing anything. Just wait for 10 minutes or so.
Make it executable: chmod u+x RunIPSet
Run it: ./RunIPSet (This could take a long time, 10-20 min)
Verify your blacklist populated: ipset list blacklist | more
Save the ipset blacklist to the local file: ipset save blacklist > /etc/sysconfig/ipset.blacklist
5. Running the whole thing at startup.
Make it executable: chmod u+x RunIPSet
Run it: ./RunIPSet (This could take a long time, 10-20 min)
Verify your blacklist populated: ipset list blacklist | more
Save the ipset blacklist to the local file: ipset save blacklist > /etc/sysconfig/ipset.blacklist
5. Running the whole thing at startup.
Save the iptables in memory to a file: iptables-save > /etc/sysconfig/iptables.cdc
Run the commands below in order to 1.Restore the blacklist from file. 2.Restore the iptables rules from file. I do this in CentOS6 by adding them to the end of /etc/rc.local
"nano /etc/rc.local" and add these commands to the bottom of the file.
ipset restore < /etc/sysconfig/ipset.blacklist
iptables-restore /etc/sysconfig/iptables.cdc
Notes and other useful commands:
If you have to modify the ipset in memory or the /etc/sysconfig/ipset.blacklist file, remove the iptables rule, destroy the ipset blacklist, create ipset blacklist again, and run the population script, save ipset memory to file, set the iptables rule again:
sudo iptables -L --line-numbers
sudo iptables -D INPUT 1
ipset destroy blacklist
ipset create blacklist hash:net
./RunIPSet (This could take a long time)
ipset save blacklist > /etc/sysconfig/ipset.blacklist
iptables -I INPUT 1 -m set --match-set blacklist src -j DROP
Remove line from ipset blacklist: ipset del blacklist <ipaddress/xx>
ipset restore < /etc/sysconfig/ipset.blacklist
iptables-restore /etc/sysconfig/iptables.cdc
I'm noticing that the temporary fail2ban iptables entries that happen to be in "iptables -L -n" are saved when you run the iptables-save and thus restored when you run the iptables-restore command. After waiting out the ban time, fail2ban will not remove these rules, I suppose because it didn't add them.
Just "nano /etc/sysconfig/iptables.cdc" and delete the lines containing those IPs so it starts clean.
If you have to modify the ipset in memory or the /etc/sysconfig/ipset.blacklist file, remove the iptables rule, destroy the ipset blacklist, create ipset blacklist again, and run the population script, save ipset memory to file, set the iptables rule again:
sudo iptables -L --line-numbers
sudo iptables -D INPUT 1
ipset destroy blacklist
ipset create blacklist hash:net
./RunIPSet (This could take a long time)
ipset save blacklist > /etc/sysconfig/ipset.blacklist
iptables -I INPUT 1 -m set --match-set blacklist src -j DROP
Remove line from ipset blacklist: ipset del blacklist <ipaddress/xx>
No comments:
New comments are not allowed.